Member-only story
Beyond IOCs: Contextualized Leads from Analytics-Driven Threat Hunts
Much is said about hunting hypothesis. How that looks like in practice?
In this post I will walk you through my thought process and share a concrete KQL hunting query for Defender for Endpoint as an example.
IOC Scanning = Hunting?
When a team takes a list of Indicators of Compromise (IOC) and compares it against matching SIEM events, does it count as threat hunting at all?
Whether you consider that hunting or not, in the end, assuming IOC hits as leads, that practice might as well be considered one step in the process.
Nevertheless, in case you have a modern SIEM, there's no excuse for not fully automating this initial step, that is, the IOC matching itself.
By automating near-real-time and retrospective scanning of IOCs, it will significantly improve your Hunting/Detection output — as long as you are able to manage and scope in a good list of IOCs.
The idea here is to go beyond the pure Threat-Intel driven approach and generate more contextualized hunting leads based on simple analytics.
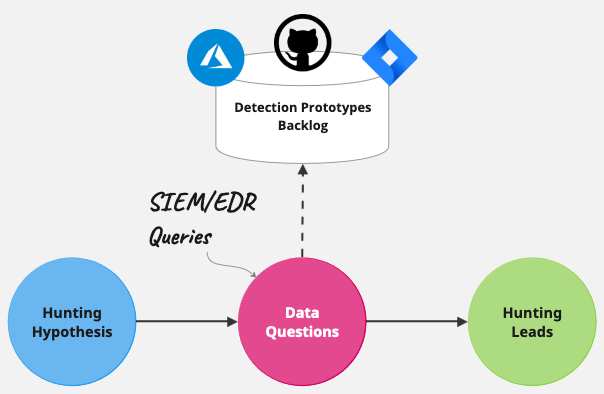
Crafting an analytics-driven hunting query
If you need a quick killer reference about Threat Hunting, I enjoyed reading the following whitepaper by Robert M. Lee and David Bianco:
Generating Hypotheses for Successful Threat Hunting
Among all the great insights from it, here's an excerpt that I found particularly useful when scoping hunt exercises:

It's easy to guess that any hunt related activity around IOCs will, at least, fit in the first item since it originates from Threat Intelligence. However, here's how the authors further explain and hint on a good hunt hypothesis:
The best way to proceed with hypothesis generation is the combination of the three different types of hypotheses.
How capable yours teams are to deliver given those hunting types?

