Member-only story
From Intelligence to Detection: A Workflow for Integrating CTI, IR, Hunting & Red Teams
In 2017, a former software tester suggested that I should consider shipping detection content by following the SDLC, and it seemed like a great idea.
Today, Detection-as-Code has evolved into one of the most valuable practices a successful engineering team can leverage as part of a Detection Use Case development process.
As expected, given the availability of Jira in the enterprise environment, that tool has become a major component for planning and tracking detection content development efforts.
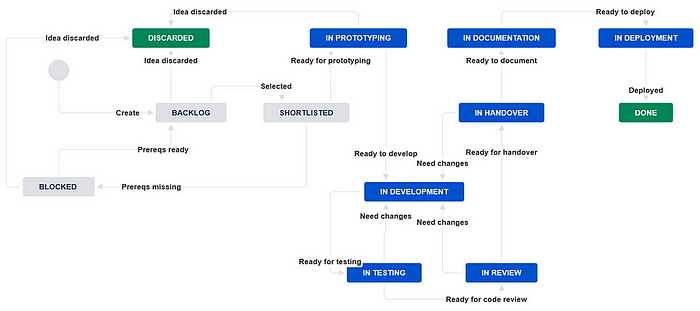
Nevertheless, just as detection demands don’t always originate from the Detection Engineering team itself, prototyping and testing new ideas should also be part of a collaborative effort with other cybersecurity teams.
Here I'm proposing a high-level, cross functional workflow that enables teams collaboration in the delivery of new detection content.
Working in silos is a real concern
Regardless of your organization’s size or whether you have dedicated teams for Threat Intelligence, IR, Hunting, or Red Teaming, there are always multiple stakeholders involved in the making of a new detection.
From the team requesting the use case to the team consuming it (e.g., the SOC), the detection engineering team must collaborate to deliver high-quality content that ultimately drives value.
I’ll briefly explore each of these practices and, in the end, propose a collaborative workflow that highlights the key role each practice plays.
Threat Intelligence as the Primary Input
Cyber Threat Intelligence (CTI) goes way beyond a list of IOCs. Still, automated IOC matching and enrichment is a must-have if you want to avoid time-consuming, manual, ad-hoc IOC scanning.
Nevertheless, just as defenders analyze CTI reports for defensive opportunities, attackers do the same to uncover potential weaknesses. This highlights the crucial role of Threat Intel and Research in our industry.
There are several drivers that inspire new detection use case ideas; here are just a few in no…

